ATT&CK Techniques to Security Events
Contents
ATT&CK Techniques to Security Events¶
Author: Jose Luis Rodriguez - @Cyb3rPandaH
Organization: Open Threat Research (OTR)
References:
Data Sources, Containers, Cloud, and More: What’s New in ATT&CK v9?
Defining ATT&CK Data Sources, Part I: Enhancing the Current State
Defining ATT&CK Data Sources, Part II: Operationalizing the Methodology
Importing Python Libraries¶
# Importing library to manipulate data
import pandas as pd
# Importing library to manipulate yaml data
import yaml
import requests
# Importing library for visualizations
from openhunt import visualizations as vis
Importing (Sub)Techniques to Security Events Mapping Yaml File¶
Using the attackcti Python library, we were able to collect all the techniques within the Enterprise matrix. After that, we mapped several security events to each data source/component/relationship. Here is the result:
yamlUrl = 'https://raw.githubusercontent.com/OTRF/OSSEM-DM/main/use-cases/mitre_attack/techniques_to_events_mapping.yaml'
yamlContent = requests.get(yamlUrl)
yamlMapping = yaml.safe_load(yamlContent.text)
mapping = pd.json_normalize(yamlMapping)
mapping.head()
| technique_id | x_mitre_is_subtechnique | technique | tactic | platform | data_source | data_component | name | source | relationship | target | event_id | event_name | event_platform | audit_category | audit_sub_category | log_channel | log_provider | filter_in | filter_in.ObjectType | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 0 | T1553.006 | True | Code Signing Policy Modification | [defense-evasion] | [Windows, macOS] | windows registry | windows registry key modification | Process modified Windows registry key | process | modified | windows registry key | 13 | RegistryEvent (Value Set). | Windows | RegistryEvent | NaN | Microsoft-Windows-Sysmon/Operational | Microsoft-Windows-Sysmon | NaN | NaN |
| 1 | T1553.006 | True | Code Signing Policy Modification | [defense-evasion] | [Windows, macOS] | windows registry | windows registry key modification | Process modified Windows registry key | process | modified | windows registry key | 14 | RegistryEvent (Key and Value Rename). | Windows | RegistryEvent | NaN | Microsoft-Windows-Sysmon/Operational | Microsoft-Windows-Sysmon | NaN | NaN |
| 2 | T1553.006 | True | Code Signing Policy Modification | [defense-evasion] | [Windows, macOS] | windows registry | windows registry key modification | Process modified Windows registry key | process | modified | windows registry key | 4670 | Permissions on an object were changed. | Windows | Object Access | Registry | Security | Microsoft-Windows-Security-Auditing | NaN | NaN |
| 3 | T1553.006 | True | Code Signing Policy Modification | [defense-evasion] | [Windows, macOS] | windows registry | windows registry key modification | Process modified Windows registry key | process | modified | windows registry key | RegistryKeyCreated | RegistryKeyCreated | Windows | None | NaN | DeviceRegistryEvents | Microsoft Defender for Endpoint | NaN | NaN |
| 4 | T1553.006 | True | Code Signing Policy Modification | [defense-evasion] | [Windows, macOS] | windows registry | windows registry key modification | Process modified Windows registry key value | process | modified | windows registry key value | 13 | RegistryEvent (Value Set). | Windows | RegistryEvent | NaN | Microsoft-Windows-Sysmon/Operational | Microsoft-Windows-Sysmon | NaN | NaN |
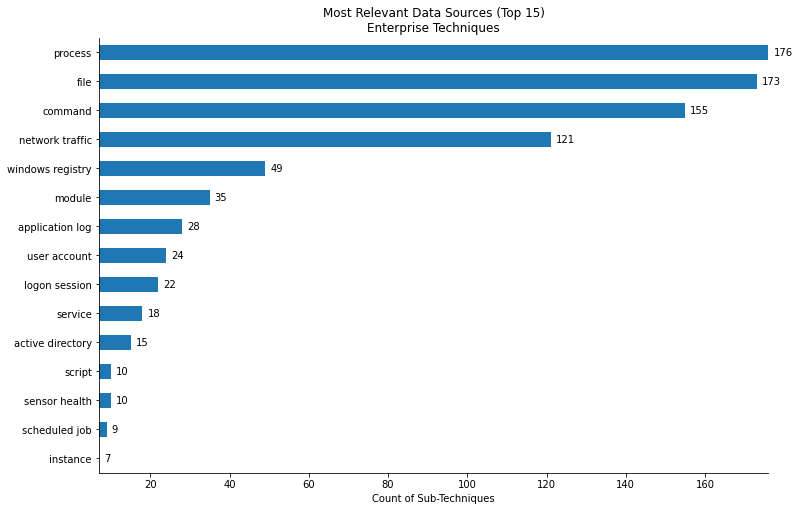
Which are the most relevant data sources for Sub-Technqiues within the Enterprise Matrix?¶
enterprise_sub = mapping[mapping['x_mitre_is_subtechnique'] == True][['technique_id','data_source','data_component']].drop_duplicates()
top15_data_source = enterprise_sub['data_source'].value_counts().nlargest(15).to_frame().reset_index()
title = 'Most Relevant Data Sources (Top 15)\nEnterprise Techniques'
vis.barh_chart(top15_data_source,'data_source','index',title, xlabel = 'Count of Sub-Techniques')
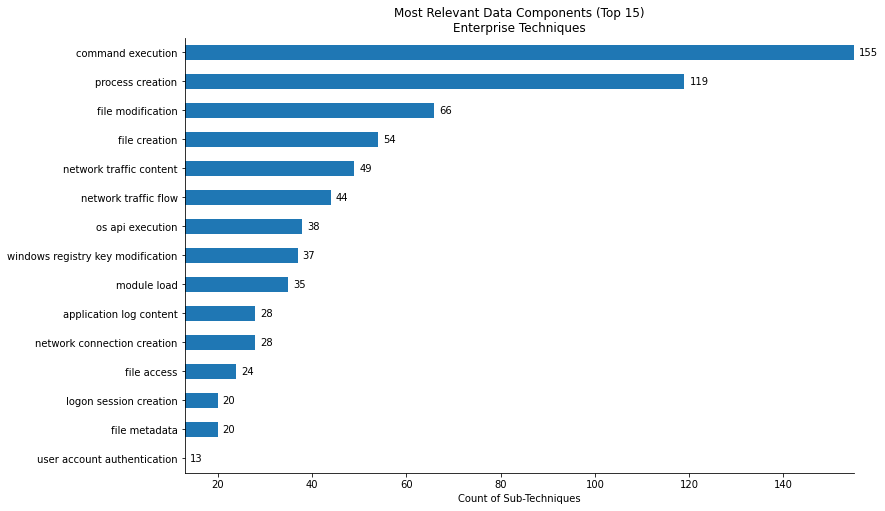
Which are the most relevant data components for Sub-Technqiues within the Enterprise Matrix?¶
enterprise_sub = mapping[mapping['x_mitre_is_subtechnique'] == True][['technique_id','data_source','data_component']].drop_duplicates()
top15_data_source = enterprise_sub['data_component'].value_counts().nlargest(15).to_frame().reset_index()
title = 'Most Relevant Data Components (Top 15)\nEnterprise Techniques'
vis.barh_chart(top15_data_source,'data_component','index',title, xlabel = 'Count of Sub-Techniques')
Use Case: OS Credential Dumping: LSASS Memory (T1003.001)¶
What are the recommended data sources?¶
mapping[mapping['technique_id']=='T1003.001'][['data_source', 'data_component']].drop_duplicates()
| data_source | data_component | |
|---|---|---|
| 4876 | process | process creation |
| 4886 | process | process access |
| 4894 | command | command execution |
| 4903 | process | os api execution |
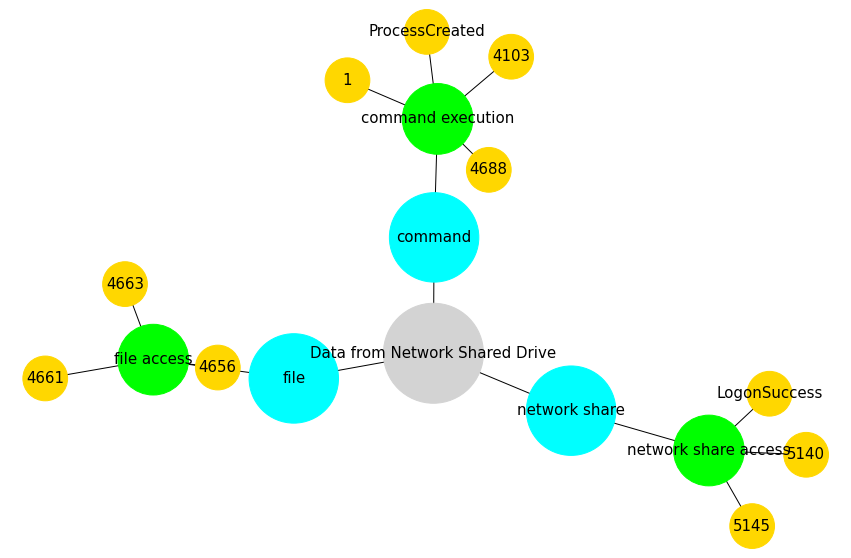
What security events can we use to get more context about this technique?¶
Network Graph
vis.attack_network_graph(mapping[(mapping['technique_id']=='T1039')])
Table
mapping[mapping['technique_id']=='T1003.001']
| technique_id | x_mitre_is_subtechnique | technique | tactic | platform | data_source | data_component | name | source | relationship | target | event_id | event_name | event_platform | audit_category | audit_sub_category | log_channel | log_provider | filter_in | filter_in.ObjectType | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4876 | T1003.001 | True | LSASS Memory | [credential-access] | [Windows] | process | process creation | Process created Process | process | created | process | 4688 | A new process has been created. | Windows | Detailed Tracking | Process Creation | Security | Microsoft-Windows-Security-Auditing | NaN | NaN |
| 4877 | T1003.001 | True | LSASS Memory | [credential-access] | [Windows] | process | process creation | Process created Process | process | created | process | 1 | Process Creation. | Windows | ProcessCreate | NaN | Microsoft-Windows-Sysmon/Operational | Microsoft-Windows-Sysmon | NaN | NaN |
| 4878 | T1003.001 | True | LSASS Memory | [credential-access] | [Windows] | process | process creation | Process created Process | process | created | process | 1 | Process Creation. | Linux | ProcessCreate | NaN | Linux-Sysmon/Operational | Linux-Sysmon | NaN | NaN |
| 4879 | T1003.001 | True | LSASS Memory | [credential-access] | [Windows] | process | process creation | Process created Process | process | created | process | ProcessCreated | ProcessCreated | Windows | None | NaN | DeviceProcessEvents | Microsoft Defender for Endpoint | NaN | NaN |
| 4880 | T1003.001 | True | LSASS Memory | [credential-access] | [Windows] | process | process creation | Process created Thread | process | created | thread | 8 | CreateRemoteThread. | Windows | CreateRemoteThread | NaN | Microsoft-Windows-Sysmon/Operational | Microsoft-Windows-Sysmon | NaN | NaN |
| 4881 | T1003.001 | True | LSASS Memory | [credential-access] | [Windows] | process | process creation | Process created Thread | process | created | thread | CreateRemoteThreadApiCall | CreateRemoteThreadApiCall | Windows | None | NaN | DeviceEvents | Microsoft Defender for Endpoint | NaN | NaN |
| 4882 | T1003.001 | True | LSASS Memory | [credential-access] | [Windows] | process | process creation | User created Process | user | created | process | 4688 | A new process has been created. | Windows | Detailed Tracking | Process Creation | Security | Microsoft-Windows-Security-Auditing | NaN | NaN |
| 4883 | T1003.001 | True | LSASS Memory | [credential-access] | [Windows] | process | process creation | User created Process | user | created | process | 1 | Process Creation. | Windows | ProcessCreate | NaN | Microsoft-Windows-Sysmon/Operational | Microsoft-Windows-Sysmon | NaN | NaN |
| 4884 | T1003.001 | True | LSASS Memory | [credential-access] | [Windows] | process | process creation | User created Process | user | created | process | 1 | Process Creation. | Windows | ProcessCreate | NaN | Linux-Sysmon/Operational | Linux-Sysmon | NaN | NaN |
| 4885 | T1003.001 | True | LSASS Memory | [credential-access] | [Windows] | process | process creation | User created Process | user | created | process | ProcessCreated | ProcessCreated | Windows | None | NaN | DeviceProcessEvents | Microsoft Defender for Endpoint | NaN | NaN |
| 4886 | T1003.001 | True | LSASS Memory | [credential-access] | [Windows] | process | process access | Process accessed Process | process | accessed | process | 10 | ProcessAccess. | Windows | ProcessAccess | NaN | Microsoft-Windows-Sysmon/Operational | Microsoft-Windows-Sysmon | NaN | NaN |
| 4887 | T1003.001 | True | LSASS Memory | [credential-access] | [Windows] | process | process access | Process accessed Process | process | accessed | process | 4663 | An attempt was made to access an object. | Windows | Object Access | Kernel Object | Security | Microsoft-Windows-Security-Auditing | [{'ObjectType': 'Process'}] | NaN |
| 4888 | T1003.001 | True | LSASS Memory | [credential-access] | [Windows] | process | process access | Process accessed Process | process | accessed | process | OpenProcessApiCall | OpenProcessApiCall | Windows | None | NaN | DeviceEvents | Microsoft Defender for Endpoint | NaN | NaN |
| 4889 | T1003.001 | True | LSASS Memory | [credential-access] | [Windows] | process | process access | Process requested access to Process | process | requested access to | process | 4656 | A handle to an object was requested. | Windows | Object Access | Kernel Object | Security | Microsoft-Windows-Security-Auditing | [{'ObjectType': 'Process'}] | NaN |
| 4890 | T1003.001 | True | LSASS Memory | [credential-access] | [Windows] | process | process access | Process requested access to Process | process | requested access to | process | 10 | Process Access. | Windows | ProcessAccess | NaN | Microsoft-Windows-Sysmon/Operational | Microsoft-Windows-Sysmon | NaN | NaN |
| 4891 | T1003.001 | True | LSASS Memory | [credential-access] | [Windows] | process | process access | Process requested access to Process | process | requested access to | process | OpenProcessApiCall | OpenProcessApiCall | Windows | None | NaN | DeviceEvents | Microsoft Defender for Endpoint | NaN | NaN |
| 4892 | T1003.001 | True | LSASS Memory | [credential-access] | [Windows] | process | process access | User accessed Process | user | accessed | process | 4663 | An attempt was made to access an object. | Windows | Object Access | Kernel Object | Security | Microsoft-Windows-Security-Auditing | [{'ObjectType': 'Process'}] | NaN |
| 4893 | T1003.001 | True | LSASS Memory | [credential-access] | [Windows] | process | process access | User accessed Process | user | accessed | process | OpenProcessApiCall | OpenProcessApiCall | Windows | None | NaN | DeviceEvents | Microsoft Defender for Endpoint | NaN | NaN |
| 4894 | T1003.001 | True | LSASS Memory | [credential-access] | [Windows] | command | command execution | Process executed Command | process | executed | command | 4688 | A new process has been created. | Windows | Detailed Tracking | Process Creation | Security | Microsoft-Windows-Security-Auditing | NaN | NaN |
| 4895 | T1003.001 | True | LSASS Memory | [credential-access] | [Windows] | command | command execution | Process executed Command | process | executed | command | 1 | Process Creation. | Windows | ProcessCreate | NaN | Microsoft-Windows-Sysmon/Operational | Microsoft-Windows-Sysmon | NaN | NaN |
| 4896 | T1003.001 | True | LSASS Memory | [credential-access] | [Windows] | command | command execution | Process executed Command | process | executed | command | 1 | Process Creation. | Linux | ProcessCreate | NaN | Linux-Sysmon/Operational | Linux-Sysmon | NaN | NaN |
| 4897 | T1003.001 | True | LSASS Memory | [credential-access] | [Windows] | command | command execution | Process executed Command | process | executed | command | 4103 | Module logging. | Windows | Executing Pipeline | NaN | Microsoft-Windows-PowerShell/Operational | Microsoft-Windows-PowerShell | NaN | NaN |
| 4898 | T1003.001 | True | LSASS Memory | [credential-access] | [Windows] | command | command execution | Process executed Command | process | executed | command | ProcessCreated | ProcessCreated | Windows | None | NaN | DeviceProcessEvents | Microsoft Defender for Endpoint | NaN | NaN |
| 4899 | T1003.001 | True | LSASS Memory | [credential-access] | [Windows] | command | command execution | User executed Command | user | executed | command | 4688 | A new process has been created. | Windows | Detailed Tracking | Process Creation | Security | Microsoft-Windows-Security-Auditing | NaN | NaN |
| 4900 | T1003.001 | True | LSASS Memory | [credential-access] | [Windows] | command | command execution | User executed Command | user | executed | command | 1 | Process Creation. | Windows | ProcessCreate | NaN | Microsoft-Windows-Sysmon/Operational | Microsoft-Windows-Sysmon | NaN | NaN |
| 4901 | T1003.001 | True | LSASS Memory | [credential-access] | [Windows] | command | command execution | User executed Command | user | executed | command | 4103 | Module logging. | Windows | Executing Pipeline | NaN | Microsoft-Windows-PowerShell/Operational | Microsoft-Windows-PowerShell | NaN | NaN |
| 4902 | T1003.001 | True | LSASS Memory | [credential-access] | [Windows] | command | command execution | User executed Command | user | executed | command | ProcessCreated | ProcessCreated | Windows | None | NaN | DeviceProcessEvents | Microsoft Defender for Endpoint | NaN | NaN |
| 4903 | T1003.001 | True | LSASS Memory | [credential-access] | [Windows] | process | os api execution | Process executed Api call | process | executed | api call | 8 | CreateRemoteThread. | Windows | CreateRemoteThread | NaN | Microsoft-Windows-Sysmon/Operational | Microsoft-Windows-Sysmon | NaN | NaN |
| 4904 | T1003.001 | True | LSASS Memory | [credential-access] | [Windows] | process | os api execution | Process executed Api call | process | executed | api call | CreateRemoteThreadApiCall | CreateRemoteThreadApiCall | Windows | None | NaN | DeviceEvents | Microsoft Defender for Endpoint | NaN | NaN |
